About OWASP Threat Dragon
Strong threat modeling tools are more important than ever in the constantly changing field of cybersecurity. Tools like OWASP Threat Dragon have become indispensable resources in the toolbox of security experts as enterprises work to safeguard their digital assets and fend off new threats. In this blog post, we examine OWASP Threat Dragon’s features, advantages, and revolutionary effect on improving the security posture of contemporary applications.
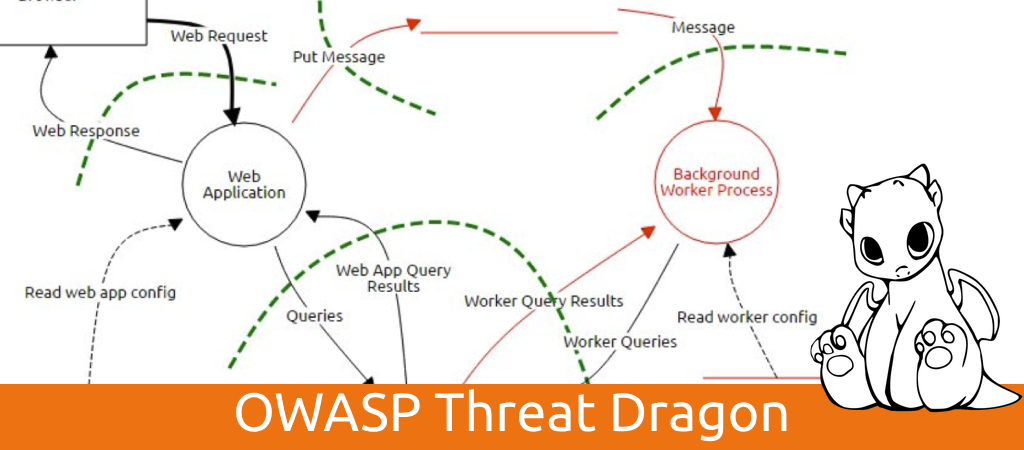
Unveiling OWASP Threat Dragon: A Visual Approach to Threat Modeling
OWASP Threat Dragon is an open-source threat modeling tool designed to simplify the process of threat modeling and risk assessment for software applications. At its core, Threat Dragon leverages visualization techniques to help security teams and developers gain a holistic understanding of the potential threats and vulnerabilities within their applications. By providing intuitive diagramming capabilities and seamless collaboration features, Threat Dragon empowers organizations to identify, prioritize, and mitigate security risks effectively.
Key Features and Capabilities
1- Intuitive Interface: Threat Dragon offers a user-friendly interface that makes it easy for users to create and visualize threat models. Its drag-and-drop functionality allows users to quickly build data flow diagrams (DFDs) and threat models, facilitating efficient threat analysis.
2- Multiple Diagramming Formats: Threat Dragon supports various diagramming formats, including DFDs, attack trees, and data flow diagrams, allowing users to choose the most suitable representation for their threat models.
3- Collaborative Workspaces: The tool provides collaborative workspaces where team members can work together in real time to create and refine threat models. This feature fosters communication and collaboration among cross-functional teams, including developers, security analysts, and stakeholders.
4- Integration with OWASP ASVS: Threat Dragon seamlessly integrates with the OWASP Application Security Verification Standard (ASVS), enabling users to align their threat models with industry best practices and security requirements.
5- Customizable Templates: The tool offers customizable templates for common threat modeling scenarios, helping users get started quickly and ensuring consistency across threat models.
6- Export and Sharing: Threat Dragon allows users to export threat models in various formats, including JSON and image files, making it easy to share and disseminate threat models across the organization.
Transformative Impact on Security Practices
OWASP Threat Dragon has a transformative impact on security practices by democratizing threat modeling and making it accessible to a wider audience. By providing a visual and collaborative platform for threat modeling, Threat Dragon breaks down silos between security teams and developers, enabling them to work together seamlessly to identify and mitigate security risks. Moreover, Threat Dragon’s integration with OWASP ASVS ensures that threat models are aligned with industry best practices, helping organizations build more secure applications from the ground up.
Conclusion
In conclusion, OWASP Threat Dragon represents a paradigm shift in the way organizations approach threat modeling and risk assessment. By leveraging visualization techniques and collaborative features, Threat Dragon empowers organizations to build a security-first mindset, ensuring that security considerations are integrated into every stage of the software development lifecycle. As cyber threats continue to evolve, tools like Threat Dragon will play a critical role in helping organizations stay one step ahead of their adversaries and build resilient, secure applications.